Credential Theft
Stolen Credentials Are a Significant Threat
The most common security incidents at NERSC are account compromises which are the result of credential theft. Unfortunately, SSH credential theft is a very common occurrence on the Internet today and, with the thousands of accounts on NERSC systems, our exposure to this threat is very high. In order to mitigate this risk, NERSC requires MFA for logging onto NERSC systems.
SSH credential theft occurs when an unauthorized person (attacker) obtains and uses valid SSH account credentials (username and password) for unauthorized access to a computer. The attacker typically obtains the valid credentials by keystroke logging a previously compromised computer. Once the attacker has gained access to the computer she may perform any number of malicious activities including hosting malicious files, attacking other computers, installing rootkits, or destroying data.
In the example below, a NERSC user is unknowingly using a previously hacked computer. It may be their own computer or it may belong to another institution. In any case, an attacker has installed a keystroke logger and is able to capture everything the user types. When the user authenticates to a NERSC computer system, the attacker is able to steal her credentials. With MFA enabled, even if a hacker obtains a user’s password through keystroke logging, they cannot use this information to access the account because a one-time password (OTP) is needed. If it weren’t for MFA, the attacker could then log into the NERSC computer at a later time and can do so from anywhere in the world.
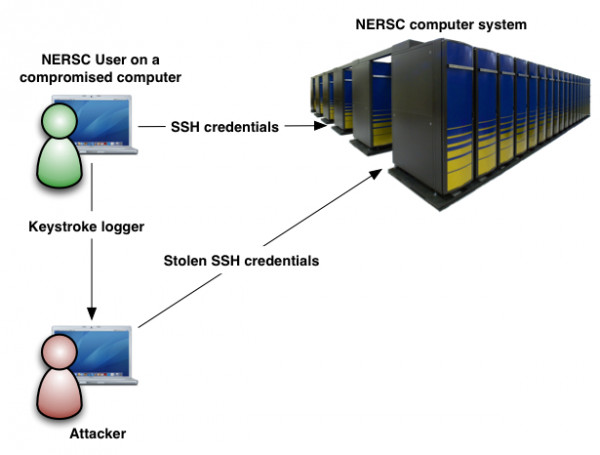
A schematic view of credential theft
Once the attacker has access to a NERSC system, even as a regular user, they will try a variety of tricks to escalate their privileges and attack other users and systems. For example, they can explore the knownhosts file and test the stolen credential on other systems. If they are able to gain root access, they can install a trojaned SSH daemon to steal credentials from other users. As shown below, once a foothold like this is established, the problem can quickly spread throughout NERSC as well as other institutions with whom we collaborate.
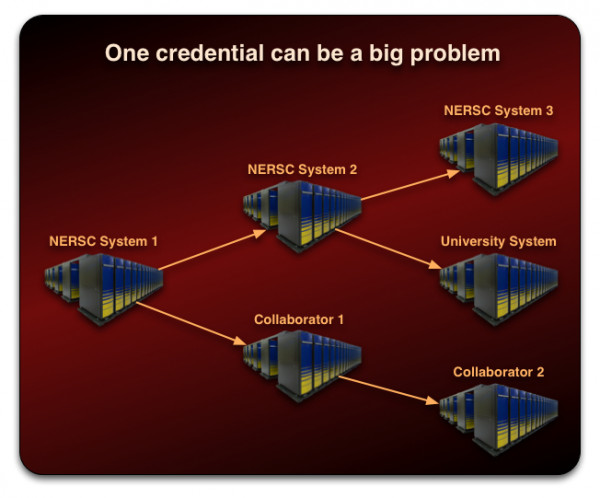
Mitigation
The best way to mitigate this threat is to enable MFA, which is mandatory for all NERSC users. Additionally, make sure the systems you login to NERSC from are secure and well maintained. Follow the recommendations throughout this tutorial. Make sure patches are applied diligently. Use antivirus and personal firewall software. If it's a laptop, never leave it unattended in a public space. If others have access to the computer make sure they understand their responsibilities as well.







